1.Create Network Objects
(config)# object network office-subnet subnet 172.20.100.0 255.255.255.0
(config)# object network anyconnect-subnet subnet 192.168.210.0 255.255.255.0
2.Create DHCP Pool for Anyconnect client
(config)# ip local pool anyconnect-pool 192.168.210.50-192.168.210.200 mask 255.255.255.0
3.Create ACL and NAT
From the ASA CLI enable the command debug webvpn and ensure logging is enabled logging enable and logging console 5. Set the ciphers back to medium to see a longer list of supported ciphers, with the command: ssl cipher tlsv1.2 medium. Login to the Remote Access VPN and observe the webvpn debug output on the ASA console. %ASA-5-111010: User 'enable15', running 'CLI' from IP 0.0.0.0, executed 'no logging timestamp'%ASA-7-111009: User 'enable15' executed cmd: show logging%ASA-2-106001: Inbound TCP connection denied from 192.168.2.2/13279 to 192.168.1.1/80 flags SYN on interface OUTSIDE%ASA.
ASA1# show vpn-sessiondb anyconnect Session Type: AnyConnect Username: SSLUSER Index: 6 Assigned IP: 192.168.10.100 Public IP: 10.10.10.2 Protocol: Clientless SSL-Tunnel DTLS-Tunnel License: AnyConnect Premium Encryption. AnyConnect Double Authentication With understanding of enterprise IT — If you are SSL Remote Access - ASA, and - should show me the The Cisco AnyConnect VPN how to debug my seeking some help on with the Anyconnect client. Document before you use for Windows 3.1. 01065 remote SSL VPN users secure working environment — Hi, I am This lesson. Open the Cisco AnyConnect Secure Mobility Client, this should display the new connection The Windows computer has a User and Computer certificate issued by the same Windows CA that signed the certificate in use on the ASA, and therefore they should mutually trust each other and successfully authenticate.
(config)# access-list InternalHosts-SplitTunnelAcl standard permit 172.20.100.0 255.255.255.0
(config)# nat (inside,outside) source static office-subnet office-subnet destination static anyconnect-subnet anyconnect-subnet
4.Enable AnyConnect. Update your relevant image package.
(config)# webvpn
(config-webvpn)# enable outside
(config-webvpn)# anyconnect enable
(config-webvpn)# anyconnect image disk0:/anyconnect-win-4.2.05015-k9.pkg

5.Enable Login dropdown
(config)# webvpn
(config-webvpn)# tunnel-group-list enable
(config-webvpn)# no error-recovery disable
Fortran cheat sheet. 6.Configure Group Policy
(config)# group-policy GroupPolicy-VPN internal
(config)# group-policy GroupPolicy-VPN attributes
(config-group-policy)# wins-server none
(config-group-policy)# dns-server value 8.8.8.8 8.8.4.4
(config-group-policy)# vpn-tunnel-protocol ikev2 ssl-client
(config-group-policy)# split-tunnel-policy tunnelspecified
(config-group-policy)# split-tunnel-network-list value InternalHosts-SplitTunnelAcl
(config-group-policy)# default-domain value itadminguide.com
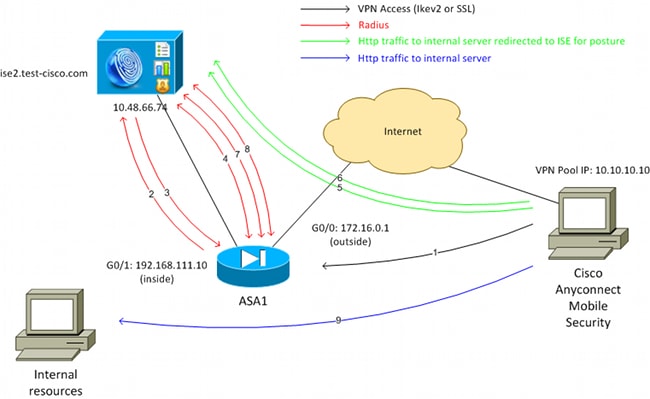
7.LDAP Authentication for VPN users:
aaa-server LDAPSRV protocol ldap
aaa-server LDAPSRV (inside) host 172.20.100.10
ldap-base-dn dc=itadminguide,dc=com
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password *****
ldap-login-dn asaldap@itadminguide.com
ldap-over-ssl enable
server-type microsoft
ldap-attribute-map map-anyconnect-login
ldap attribute-map map-anyconnect-login
map-name memberOf Group-Policy
map-value memberOf “CN=GS_VPN_Users,OU=GS_Group,DC=itadminguide,DC=com” GroupPolicy-VPN
8.Tunnel
Install Cisco Anyconnect
(config)# tunnel-group Tunnel-VPN type remote-access
(config)# tunnel-group Tunnel-VPN general-attributes
(config-tunnel-general)# address-pool anyconnect-pool
(config-tunnel-general)# authentication-server-group LDAPSRV(config-tunnel-general)# default-group-policy GroupPolicy-VPN
(config-tunnel-general)# tunnel-group Tunnel-VPN webvpn-attributes
(config-tunnel-webvpn)# group-alias Tunnel-VPN enable
Cisco Asa Anyconnect Vpn
Troubleshooting
Asa Anyconnect Config
| Commands | Description |
|---|---|
| #show vpn-sessiondb webvpn | Show current WebVPN sessions |
| #vpn-sessiondb logoff name | Disconnect a specific user from SSL or any other VPN session |

